In May of 2017, the WannaCry ransomware virus infected computer systems in at least 150 countries, including 81 British hospitals, leading to 19,500 canceled medical appointments, 600 locked computers and 5 hospitals that had to direct ambulances elsewhere. However, the most frightening news to come from the attack was that the ransomware virus also hit a medical device in a US hospital. The device monitored the amount of a “contrast agent” injected into the patient to improve the imaging quality of MRI scans. This ransomware didn’t threaten patient safety directly because all it could do was stop the device from working, but it did prove that medical devices are also at risk of cyberattacks and could potentially cause mistakes and delays in care, especially if a virus goes unnoticed.
It often takes cyberattacks like this one for companies to start taking action. By then the damage is done, so it’s important to know your role in protecting your device from hackers. Taking the right precautions ahead of time can save your device’s reputation and potentially save lives as hackers become more powerful going after the vulnerabilities in pacemakers and insulin pumps. To help you with this task I’ve done some research and put together some ways you can protect your medical device from cyberattacks.
Ways to Protect Your Medical Device from Hackers
Assess the Risk of a Cybersecurity Vulnerability
The FDA encourages medical device manufacturers to assess the exploitability of the cybersecurity vulnerability and the severity of patient harm from that exploitability, so manufactures can determine how to respond to the risk.
To assess exploitability the FDA suggests using a tool or similar scoring system to the Common Vulnerability Scoring System, Version 3.0.
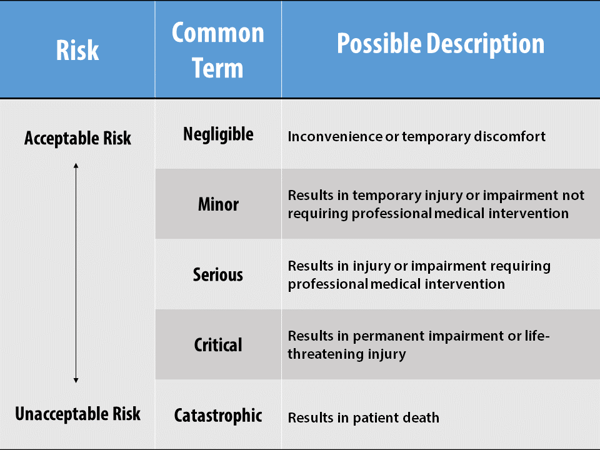
For assessing the severity of patient harm the FDA suggests basing the severity levels off the ones described in ANSI/AAMI/ISO 14971: 2007/®2010: Medical Devices – Application of Risk Management to Medical Devices:
Build Your Device with Cybersecurity in Mind
Make room for any expected cybersecurity components you’re planning to add or update in the future. Also, have a cybersecurity plan in place in case your device ever does experience a security breach.
Share Information to Keep the Industry Ahead of Hackers
Currently some medical device reporting is mandatory, but there hasn’t been as much incentive to report cybersecurity vulnerabilities. However, it’s a great way to take an active role in protecting the industry from threats. The FDA has been working on a system to share cyber vulnerabilities and threats between the NH-ISAC, MDISS, and FDA in a trusted space where they can quickly take action to alleviate the risks. You can currently see reported cybersecurity vulnerabilities on the FDA’s Safety Communications page.
Keep Your Medical Device Software Up to Date
Systems with updated security patches are rarely vulnerable because it is harder to hack the newest software. Also in many cases, changes made to solely strengthen cybersecurity are not likely to require submission of a new 501(k). (FDA - Deciding When to Submit a 510(k) for a Software Change to an Existing Device)
Educate the End Users about Cybersecurity Best Practices
Provide easy-to-understand cybersecurity awareness tips, or ongoing education, to the staff that will be using your medical device. Simple tips like regularly changing passwords, picking strong passwords, as well as education on identifying hazards like phishing, ransomware, and malware can go a long way.
These were just a few suggestions I found to protect your medical device from hackers. However, you can find detailed information on this FDA Guidance Document on the Postmarket Management of Cybersecurity in Medical Devices. Cybercrime is expected to cost the world $6 trillion annually by 2021, so it’s not going away anytime soon. Will you be prepared when a cyber threat or attack comes for your device?
If you have questions about cybersecurity for you medical device, or need a custom medical cart designed for your cybersecurity needs, contact us today.